紧接上一篇,让openvpn读取本地文件中的用户名密码,通过判断用户名密码是否存在文件中进行认证,搭建openvpn环境就不多做说明了,只要把openvpn搭建好,客户端能够连接就可以了。
1、修改openvpn配置文件
1 | vi /etc/server.conf |
编辑/etc/server.conf文件,并添加如下内容:
1 | auth-user-pass-verify /etc/openvpn/checkpsw.sh via-env |
例如:
1 | [root@openVPN openvpn-2.0.9]# cat /etc/server.conf |
2、下载用户验证脚本checkpsw.sh
文件的官方下载地址是: http://openvpn.se/files/other/checkpsw.sh
但是可能现在已经无法下载了,如果无法下载就把下面的内容拷贝到一个文件中,然后改名为checkpw.sh即可,当然网上有很多地方有这个脚本,所以脚本的下载不是什么问题。
1 | [root@openvpn ~]# cat checkpsw.sh |
3、创建用户名密码文件
1 | cp /root/checkpsw.sh /etc/openvpn/ |
4、修改客户端配置文件
注释掉cert和key(客户端不需要crt和key文件,但是需要服务器的CA证书)
1 | ;cert eva.crt |
添加如下内容:
1 | auth-user-pass |
例如:
1 | client |
5、客户端连接测试
创建一个新的名为“psw”的连接,里面的内容就是步骤4贴出来的,目录中只需要放服务器端CA证书即可:
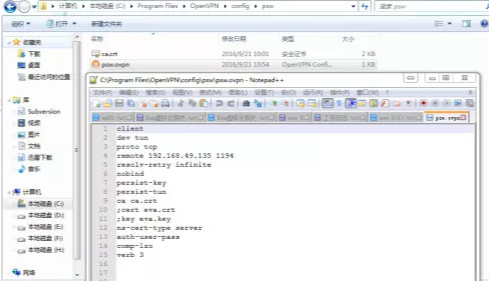
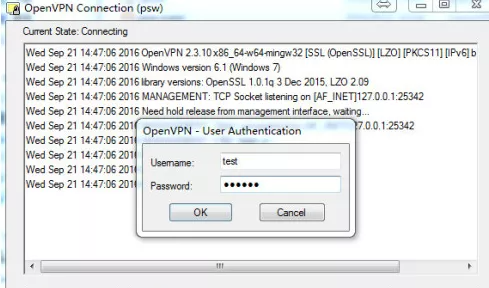
客户端点击连接之后,弹出窗口,这里输入pws-file文件中的用户名密码:
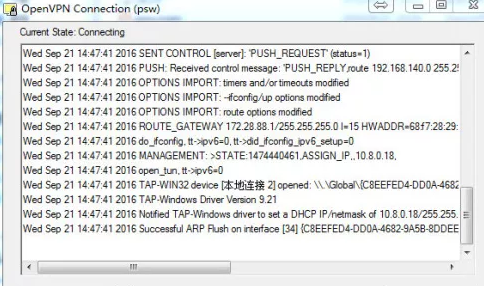
认证通过,成功连接:
6、检查日志:
查看用户名密码认证产生的日志:
1 | [root@open*** ~]# cat /var/log/openvpn/openvpn-password.log |
查看openvpn状态日志:
1 | [root@open*** open***-2.0.9]# tail -f /opt/tools/open***-2.0.9/easy-rsa/2.0/open***-status.log |

