今天连接openVPN一直报错,连接失败,查看连接错误日志如下:
1 | Sat Oct 08 11:04:24 2022 VERIFY ERROR: depth=0, error=certificate has expired: CN=server |
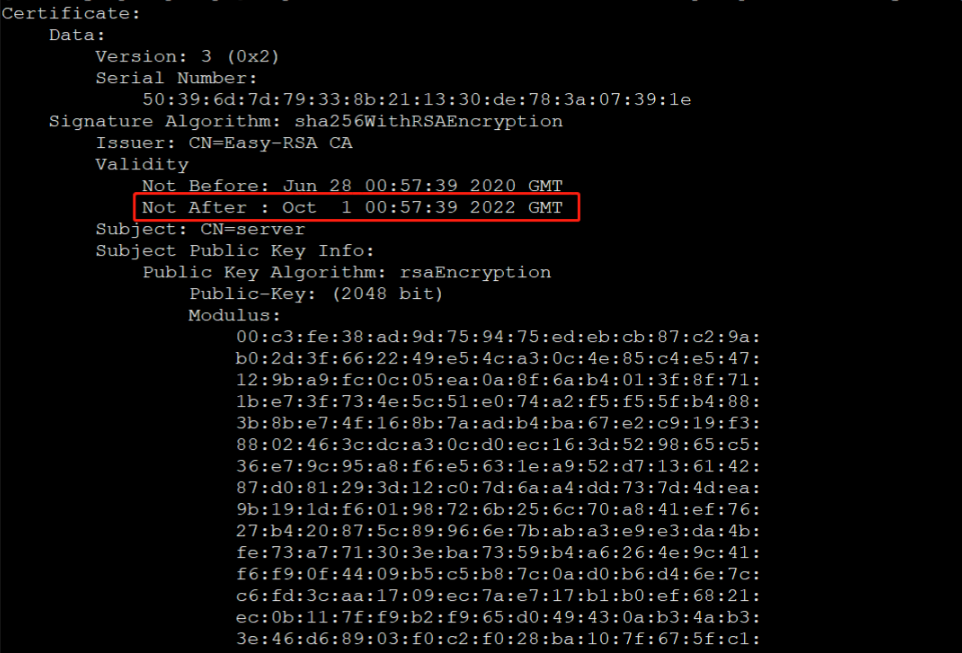
从日志消息得知证书过期,到服务器查看证书到期时间:
1 | openssl x509 -noout -text -in /etc/openvpn/server/easy-rsa/pki/issued/server.crt |
看到证书确实到期了:
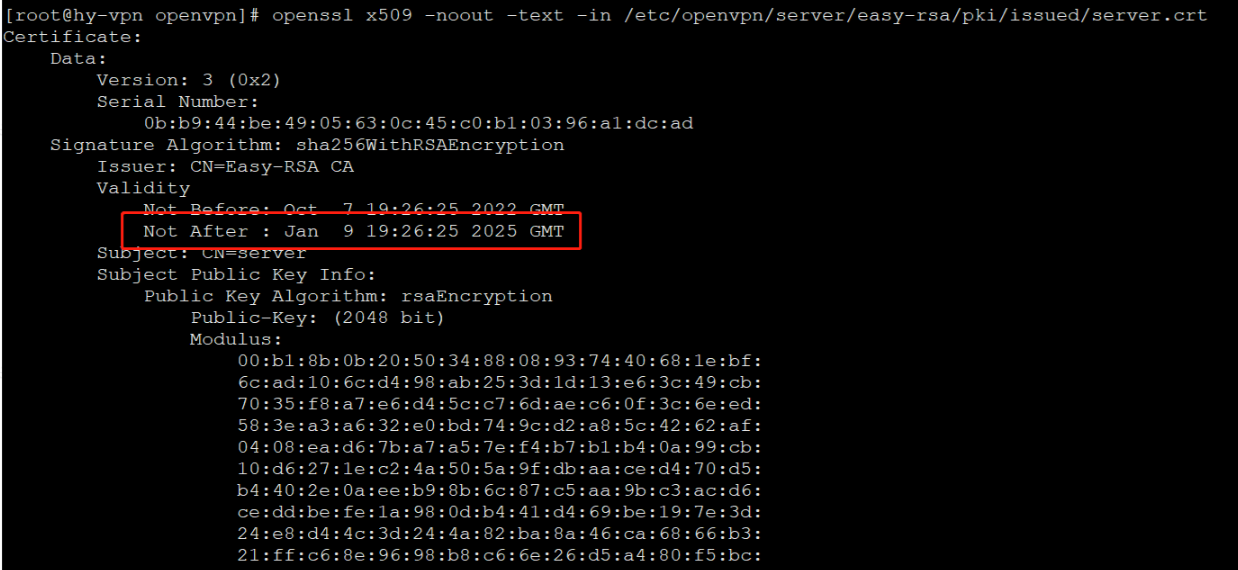
解决方法1:
续期证书:
1 | ./easyrsa renew server nopass |
重新查看证书到期时间:
验证证书有效性:
1 | [root@xxx cert_new]# openssl verify -CAfile ca.crt -purpose sslserver server.crt |
证书续期成功,重启服务重新连接即可。
ps:Windows连接面板没反应可把log文件删除再重新连接。
解决方法2:
把相关证书文件重新生成一次(可生成长时间不到期的证书):
首先新建一个空文件夹,用于存放新证书相关文件:
1 | mkdir /etc/openvpn/cert_new |
当时搭建OpenVPN时,使用的是easy-rsa进行证书生成,因此将之前的easy-rsa拷贝至cert_new文件夹:
1 | cp -r /etc/openvpn/easy-rsa /etc/openvpn/cert_new |
进入新的easy-rsa文件夹,删除旧的pki文件夹:
1 | rm -rf pki |
使用“easyrsa”命令新建pki目录:
1 | [root@xxx easy-rsa] |
生成ca证书:
1 | [root@xxx easy-rsa]# ./easyrsa --batch build-ca nopass |
生成服务端证书(前面的环境变量代表证书超时天数为3650天):
1 | [root@xxx easy-rsa] |
生成客户端证书:
1 | [root@xxx easy-rsa] |
生成crl.pem文件:
1 | [root@xxx easy-rsa]# EASYRSA_CRL_DAYS=3650 ./easyrsa gen-crl |
将这些文件统一复制到/etc/openvpn/cert_new目录:
1 | cp pki/ca.crt pki/private/ca.key pki/issued/server.crt pki/private/server.key pki/crl.pem /etc/openvpn/cert_new |
为避免权限问题,将crl.pem的所有者改为nobody:
1 | chown nobody:nobody crl.pem |
进入/etc/openvpn/cert_new目录,使用openssl命令验证证书有效性:
1 | [root@xxx cert_new]# openssl verify -CAfile ca.crt -purpose sslserver server.crt |
生成OpenVPN所需的secret文件ta.key:
1 | openvpn --genkey --secret ta.key |
将所有需要的文件复制到/etc/openvpn:
1 | cp ca.crt ca.key crl.pem easy-rsa server.crt server.key ta.key /etc/openvpn |
重启OpenVPN服务,即可使OpenVPN加载新的证书文件。

